Hacking group also employed an IE zero-day in opposition to stability researchers

An Internet Explorer zero-day vulnerability has been learned utilized in recent North Korean attacks versus security and vulnerability scientists.
Final month, Google disclosed that the North Korean condition-sponsored hacking team identified as Lazarus was conducting social engineering assaults in opposition to security scientists.
To perform their assaults, the danger actors produced elaborate on the net ‘security researcher’ personas that would then use social media to get in touch with effectively-regarded protection researchers to collaborate on vulnerability and exploit development.
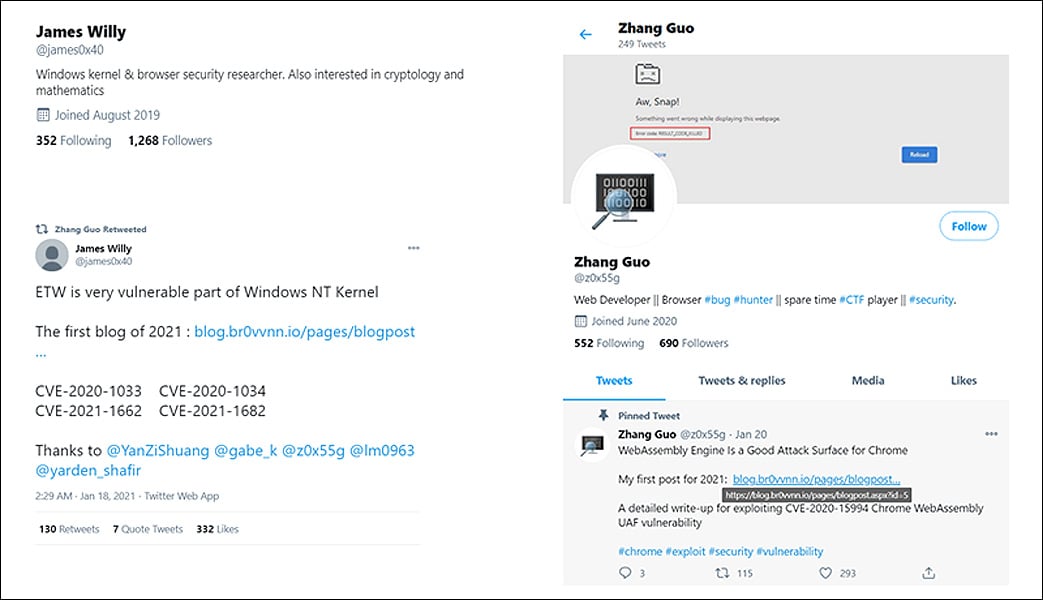
As section of this collaboration, the attackers despatched destructive Visible Studio Projects and backlinks to internet websites hosting exploit kits that would put in backdoors on the researcher’s pcs.
Microsoft also described they had been tracking the attack and experienced viewed Lazarus sending MHTML data files to researchers containing malicious javascript. At the time of their investigation, the command and handle server was down, and Microsoft could not look into further payloads.
Internet Explorer zero-day used in assaults
Right now, South Korean cybersecurity company ENKI reported that Lazarus focused security scientists on their group with MHTML files in this social engineering marketing campaign.
Even though they state that the attacks unsuccessful, they analyzed the payloads downloaded by the MHT file and learned it contained an exploit for an World-wide-web Explorer zero-working day vulnerability.
An MHT/MHTML file, usually identified as MIME HTML, is a distinctive file format used by Online Explorer to store a web website page and its resources in a single archive file.
The MHT file despatched to ENKI researchers contained what was allegedly a Chrome 85 RCE exploit and was named ‘Chrome_85_RCE_Entire_Exploit_Code.mht.’
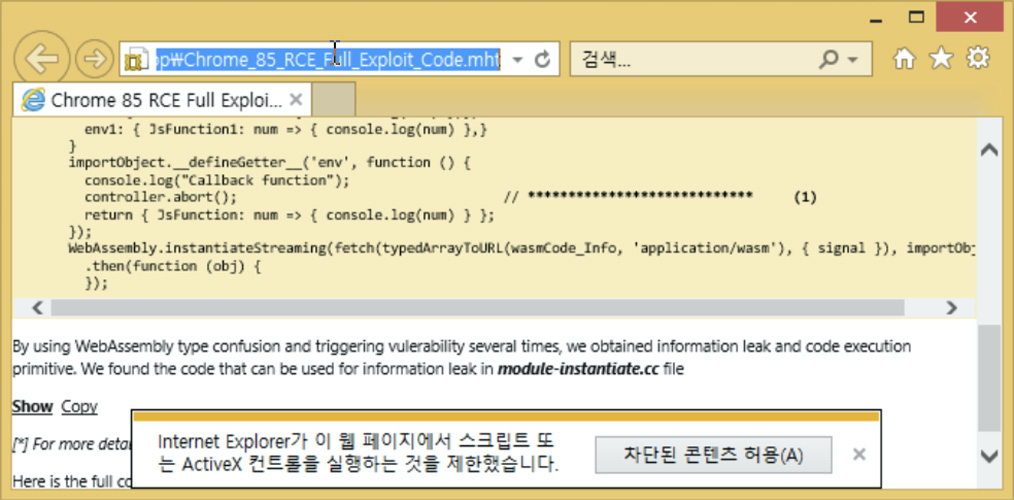
When the MHT/MHTML file was opened, Internet Explorer quickly released to screen the contents of the MHT file. If script execution was allowed, ENKI suggests that destructive javascript would download two payloads, with a person containing a zero-day from Net Explorer.
This exploit abuses a double-no cost bug in IE 11, allowing the attackers to upload a record of the jogging approach, display captures, and network info to their command and regulate server. It would then down load and execute more destructive code from the C2 server to be executed.
ENKI advised BleepingComputer that they have documented the bug to Microsoft and have been later contacted by a Microsoft personnel requesting far more information.
Acros CEO and 0patch co-founder Mitja Kolsek told BleepingComputer that he was ready to reproduce the World wide web Explorer zero-day PoC noted by ENKI.
Dependent on tweets from other stability researchers, ENKI advised BleepingComputer that they believe other scientists know of this IE 11 zero-day.
https://t.co/hN4QTkVovk pic.twitter.com/rbQFTuAfaw
— b0ring (@dnpushme) February 4, 2021
Microsoft explained to BleepingComputer that they investigate just about every report and will supply an update in the long run.
“Microsoft has a buyer determination to examine reported protection troubles and we will give updates for impacted units as quickly as doable.”- a Microsoft spokesperson.







